Secure Multi-Party Computation Study
#MPC
2024-04-08
What's Secure multi-party computation?
Various applications in various real-world problems
Various dimensions of the SMPC study
Dimension 1: Form of Function Abstraction
Boolean vs. Arithmetic
Dimension 2: Network Type
Synchronous vs. Asynchronous
Dimension 3: Corruption Capacity
Threshold vs. Non-Threshold
Dimension 4: Corruption Power
Bounded vs. Unbounded
Dimension 5: Corruption Characteristic
Passive/Semi-honest (vs. Crash/fail-stop) vs. Active/Malicious(/Byzantine)
Dimension 6: Corruption Time
Static vs. Adaptive
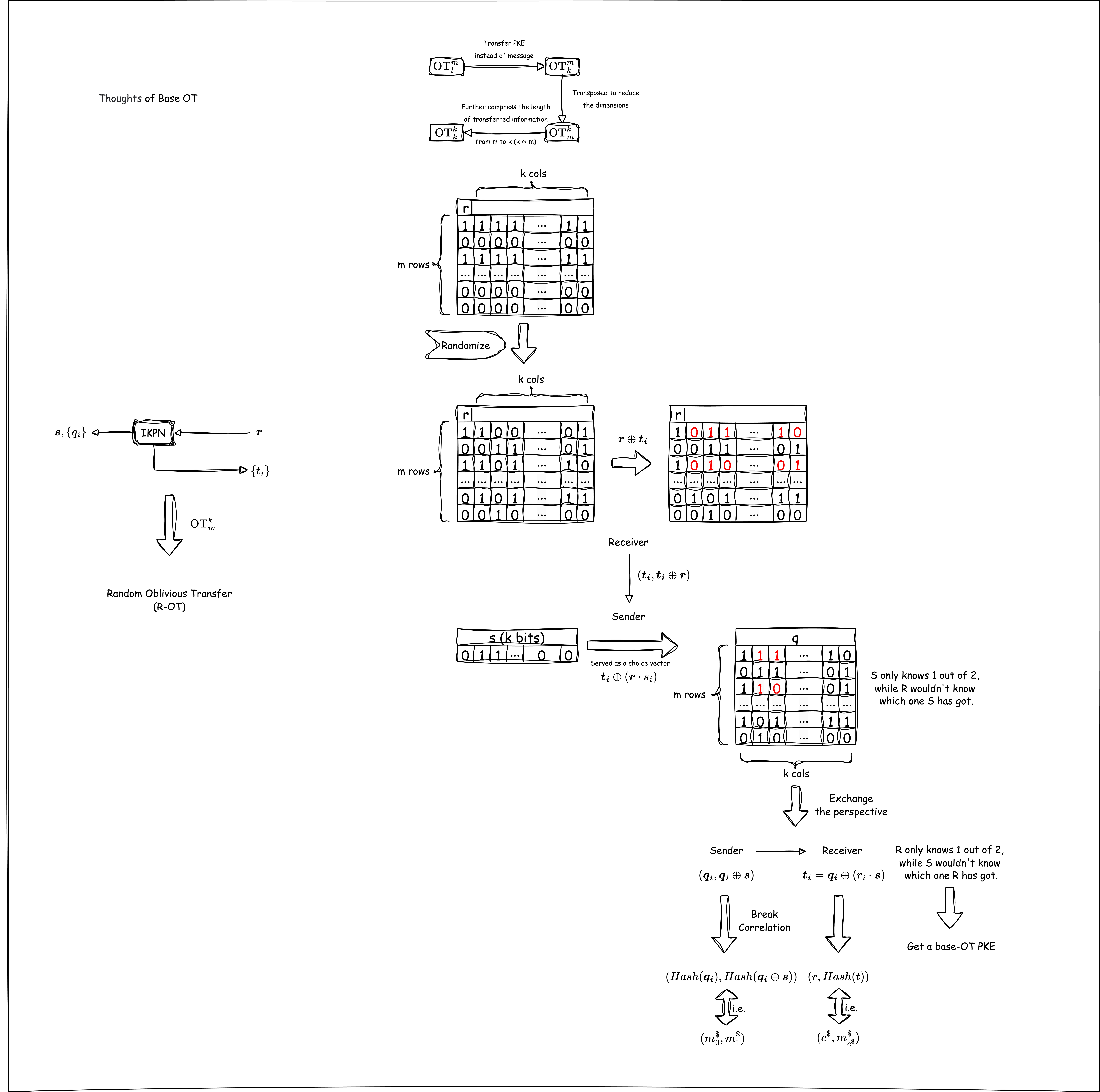
What's the IKNP Protocol
From n to k
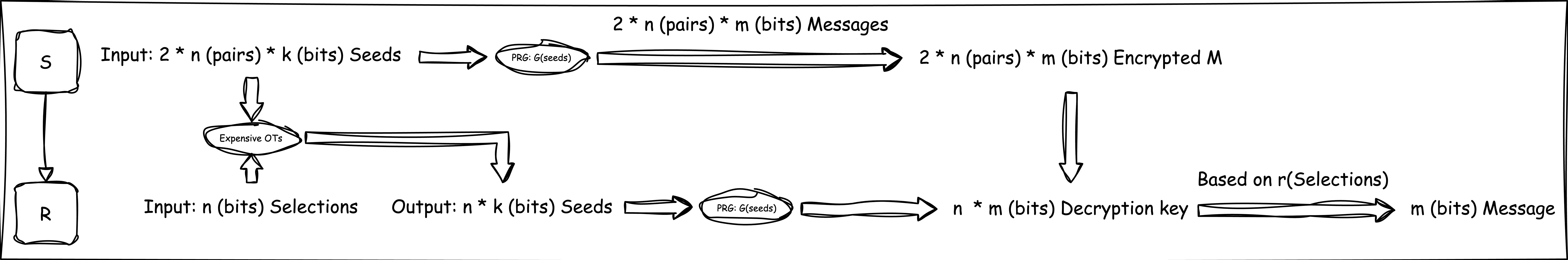
Details in IKNP protocol